DMVPN faza 1 + IPSEC – konfiguracja
by admin · Styczeń 2, 2018
We wpisie https://kubsoo.github.io/rsnet-website/dmvpn-faza-1-konfiguracja/ pokazałem jak skonfigurować DMVPN w fazie 1 z dynamicznymi mapowaniami NHRP. W tym wpisie pokażę jak do tak przygotowanej konfiguracji dodać konfigurację IPSEC, tak żeby łączność pomiędzy urządzeniami była zabezpieczona przy wykorzystaniu IPSEC.
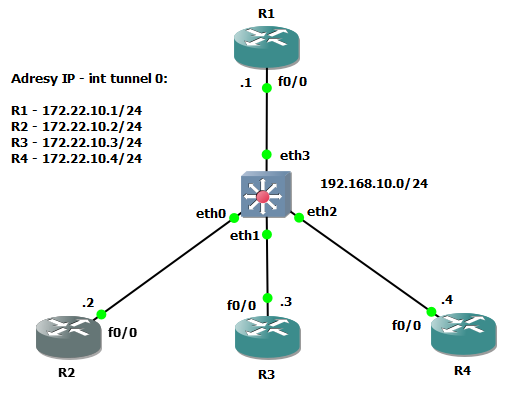
Przypomnijmy jeszcze raz topologię oraz konfigurację DMVPN w fazie 1 z dynamicznymi mapowaniami NHRP.
Topologia
Konfiguracja DMVPN
R1
hostname HUB
!
interface Tunnel0
ip address 172.22.10.1 255.255.255.0
ip nhrp network-id 123
tunnel source FastEthernet0/0
tunnel mode gre multipoint
!
interface FastEthernet0/0
ip address 192.168.10.1 255.255.255.0
!
R2
hostname SPOKE1
!
interface Tunnel0
ip address 172.22.10.2 255.255.255.0
ip nhrp map 172.22.10.1 192.168.10.1
ip nhrp network-id 123
ip nhrp nhs 172.22.10.1
tunnel source FastEthernet0/0
tunnel destination 192.168.10.1
!
interface FastEthernet0/0
ip address 192.168.10.2 255.255.255.0
!
R3
hostname SPOKE2
!
interface Tunnel0
ip address 172.22.10.3 255.255.255.0
ip nhrp map 172.22.10.1 192.168.10.1
ip nhrp network-id 123
ip nhrp nhs 172.22.10.1
tunnel source FastEthernet0/0
tunnel destination 192.168.10.1
!
interface FastEthernet0/0
ip address 192.168.10.3 255.255.255.0
!
R4
hostname SPOKE3
!
interface Tunnel0
ip address 172.22.10.4 255.255.255.0
ip nhrp map 172.22.10.1 192.168.10.1
ip nhrp network-id 123
ip nhrp nhs 172.22.10.1
tunnel source FastEthernet0/0
tunnel destination 192.168.10.1
!
interface FastEthernet0/0
ip address 192.168.10.4 255.255.255.0
!
KONFIGURACJA IPSEC
Przed przystąpieniem do konfigurowania IPSEC sprawdźmy jak wygląda ruch w DMVPN widziany na interfejsie fa0/0 routera R1. Posłużymy się do tego wiresharkiem:
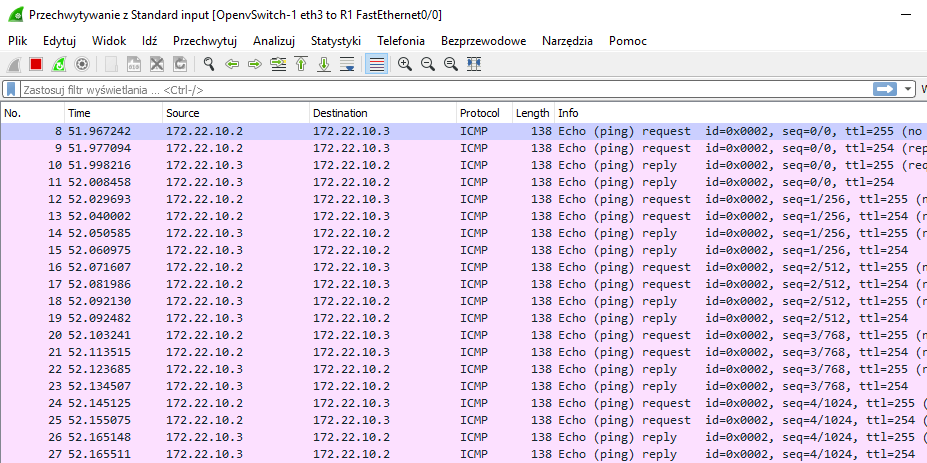
Po uruchomieniu wiresharka spingujmy router R3 (SPOKE-2) z routera R2 (SPOKE-1). W tym celu wydajmy polecene ping 172.22.10.3 na routerze R2 (SPOKE-1).
SPOKE1#ping 172.22.10.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.22.10.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/40/60 ms
Sprawdźmy jak wygląda ten ruch w wiresharku:
Widzimy, że ruch nie jest szyfrowany i możemy go podsłuchać. Spróbujmy go teraz zabezpieczyć przy pomocy IPSECa.
Konfiguracja IPSEC na każdym routerze wygląda tak samo:
R1 (HUB), R2 (SPOKE1), R3 (SPOKE2), R4 (SPOKE3)
crypto isakmp policy 10
encr aes
authentication pre-share
group 2
crypto isakmp key cisco123 address 0.0.0.0
!
!
crypto ipsec transform-set TSET esp-aes esp-sha-hmac
mode transport
!
crypto ipsec profile IPSEC_PROFILE
set transform-set TSET
!
int tunnel 0
tunnel protection ipsec profile IPSEC_PROFILE
Po skonfigurowaniu IPSEC sprawdźmy czy zestawił się on poprawnie (isakmp sa i ipsec sa). Wystarczy, że dokonamy sprawdzenia na routerze R1 (HUB), ponieważ routery R2, R3, R4 zestawiają tunele tylko z nim.
R1 (HUB)
HUB#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
192.168.10.4 192.168.10.1 QM_IDLE 1005 ACTIVE
192.168.10.1 192.168.10.4 QM_IDLE 1004 ACTIVE
192.168.10.1 192.168.10.3 QM_IDLE 1003 ACTIVE
192.168.10.1 192.168.10.2 QM_IDLE 1001 ACTIVE
192.168.10.2 192.168.10.1 QM_IDLE 1002 ACTIVE
192.168.10.3 192.168.10.1 QM_IDLE 1006 ACTIVE
HUB#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 192.168.10.1
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.10.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (192.168.10.3/255.255.255.255/47/0)
current_peer 192.168.10.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 6, #pkts encrypt: 6, #pkts digest: 6
#pkts decaps: 7, #pkts decrypt: 7, #pkts verify: 7
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.10.1, remote crypto endpt.: 192.168.10.3
path mtu 1500, ip mtu 1500, ip mtu idb (none)
current outbound spi: 0x4D074ABE(1292323518)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xA8B99213(2830733843)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 7, flow_id: 7, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4329808/3210)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x81E2FE13(2179137043)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 9, flow_id: 9, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4282574/3210)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x7BDEB7FE(2078193662)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 17, flow_id: 17, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4298093/3218)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x2B6C154D(728503629)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 8, flow_id: 8, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4329808/3210)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x1A5D7249(442331721)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 10, flow_id: 10, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4282574/3210)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x4D074ABE(1292323518)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 18, flow_id: 18, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4298093/3218)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.10.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (192.168.10.2/255.255.255.255/47/0)
current_peer 192.168.10.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 6, #pkts encrypt: 6, #pkts digest: 6
#pkts decaps: 7, #pkts decrypt: 7, #pkts verify: 7
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.10.1, remote crypto endpt.: 192.168.10.2
path mtu 1500, ip mtu 1500, ip mtu idb (none)
current outbound spi: 0x72B18574(1924236660)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x532102AC(1394672300)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 1, flow_id: 1, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4349860/3205)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0xA0B95616(2696500758)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 3, flow_id: 3, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4203743/3205)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x3D891B1C(1032395548)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 5, flow_id: 5, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4371005/3208)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x8888EE44(2290675268)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 2, flow_id: 2, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4349860/3205)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x85FE093(140501139)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 4, flow_id: 4, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4203743/3205)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x72B18574(1924236660)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 6, flow_id: 6, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4371005/3208)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.10.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (192.168.10.4/255.255.255.255/47/0)
current_peer 192.168.10.4 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 1, #pkts encrypt: 1, #pkts digest: 1
#pkts decaps: 2, #pkts decrypt: 2, #pkts verify: 2
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 192.168.10.1, remote crypto endpt.: 192.168.10.4
path mtu 1500, ip mtu 1500, ip mtu idb (none)
current outbound spi: 0xD87AECE3(3631934691)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xFCF21C61(4243725409)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 11, flow_id: 11, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4192015/3216)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x8DACF8C3(2376923331)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 13, flow_id: 13, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4370183/3216)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0xF7D288AB(4157769899)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 15, flow_id: 15, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4608000/3218)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xE7B4AE5B(3887378011)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 12, flow_id: 12, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4192015/3216)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x3D9E28E5(1033775333)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 14, flow_id: 14, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4370183/3216)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0xD87AECE3(3631934691)
transform: esp-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 16, flow_id: 16, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4608000/3218)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
Jak widać z wyników powyższych komend wszystkie tunele zestawiły się poprawnie.
WERYFIKACJA
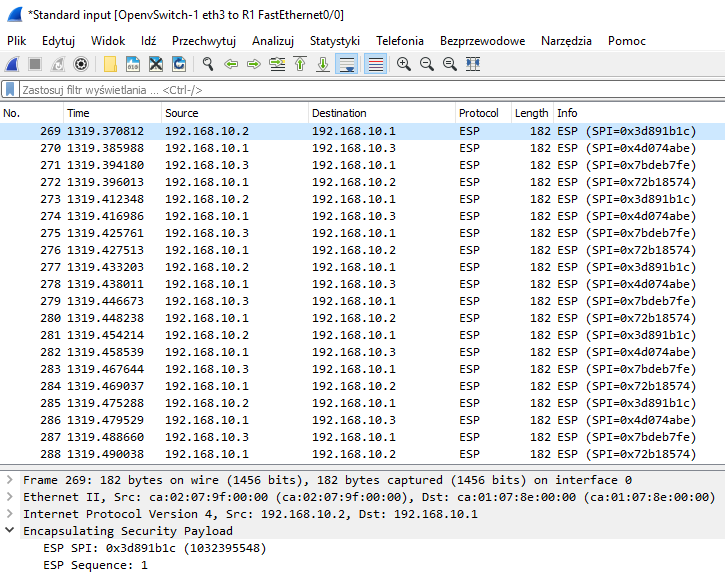
Sprawdźmy teraz co widać w wiresharku przy pingowaniu routera R3 (SPOKE-2) z routera R2 (SPOKE-1).
SPOKE1#ping 172.22.10.3
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.22.10.3, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/40/60 ms
PODSUMOWANIE
Jak widać zgodnie z teorią IPSEC w wiresharku przy pingowaniu widzimy adresy 192.168.10.X (ponieważ skonfigurowaliśmy IPSEC w trybie transportowym), ponadto nie widzimy jaki ruch jest przesyłany. Widzimy tylko pakiety ESP które składają się z ESP SPI oraz numeru sekwencyjnego. DMVPN w połączeniu z IPSEC jest bardzo dobrą kombinacją do budowania skalowanych sieci VPN między oddziałami firmy, ponieważ przy dodawaniu nowego oddziału (SPOKE) dzięki zastosowaniu DMVPN nie musimy nic konfigurować na naszym HUBie i taki nowy oddział po skonfigurowaniu będzie miał łączność pomiędzy innymi oddziałami a IPSEC pozwoli dodatkowo zabezpieczyć transmisję.